Note: This post is super-fast publish, and will be changing. Turns out its going to be gnarly to totally change the Exchange OrganziationalConfig to block EWS that we don't want. I'm working with the SEND product team to identify User Agent strings for blocking in EWS, etc.
Identified! User Agent string for blocking Send in EWS policy is "MicrosoftSend/*"
Reference is here:
http://blogs.technet.com/b/matabra/archive/2012/08/23/block-mobile-apps-that-use-exchange-web-services.aspx
Background:
Today (nice late birthday present, btw), Microsoft Garage released an App for iOS that mimics IM/Texting functionality, but really just uses Exchange Web Services and some special handling.
As such, it does not require ActiveSync, and therefore has no security policy. See the FAQ
here (requires Yammer, unfortunately)
So basically, this app is out there and is a giant hole (and honestly, anyone could write an EWS application that blows past ActiveSync security policies). But this has Microsoft's name on it, so we're going to get proactive.
So, I've got my iPad with no device partnership in ActiveSync (I just removed it, I had the Outlook app installed). I've also cleared the passcode which was an ActiveSync policy requirement.
Now I install SEND on the iPad (it's technically an iPhone app, but I'm not making all of these policy changes on my main phone). Sign in with my O365 creds, and Voila! an email client using EWS and no passcode/lock policy. There is no ActiveSync partnership for this device, and therefore not putting in device restrictions, and I can still send "Send" messages freely using EWS.
I also removed the Outlook App from the device entirely, and I can still execute Directory searches using EWS. With no device security policy in place, I can query the name of my org's CEO and Send him a short diatribe about what I think of his mother.
No bueno.
So, what do we do?
The SEND app needs to be blocked in EWS policy, which can be set per-user using Set-CASMailbox, or org-wide using Set-OrganizationalConfig. Here, an important decision needs to be made. Do you whitelist or blacklist applications in EWS? Well, this is going to vary based on your organization. There are some built-in properties for Outlook, MacOutlook, and Entourage. Otherwise, use EWSApplicationAccessPolicy [EnforceBlockList | EnforceAllowList].
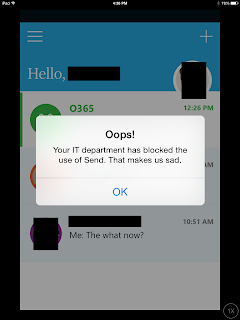
To test all of this nonsense, I set my own mailbox to disallow the Send App. Set-CASMailbox -Identity mailbox@domain.com -EwsApplicationAccessPolicy EnforceBlockList -EwsBlockList @{Add="MicrosoftSend/*", "LinkedInEWS"} . (I won't go into why I'm blocking LinkedIn, but I do suggest you search it).
Success! Now my iPad reports frowny face when an attempt is made to use Send.
Yeah, well, it makes me sad when products are released and hyped on Yammer when they are not on the roadmap, break security policies, and make my life harder.